Google Pixel 9 released: The Best Time to Upgrade to the Pixel 8 (and GrapheneOS)
The Google Pixel 9 has just been released, making this probably the best time to snap up its predecessor, the Pixel 8 – a solid phone with years-long software support – and switch to GrapheneOS along the way!
The title of this post is admittedly more clickbait than the average reader might be used to reading on this site, and a sarcastic nudge to all the tech outlets pushing what feels like mostly ChatGPT-generated Pixel 9 content right now. However, in its essence, the title isn’t far from the truth. With Google’s yearly release cycle of its more flagship-type phones, namely the Pixel and Pixel Pro series, the release of the Pixel 9 just put a big dent into the prices of the previous generation phones, making them more attractive to anyone looking to reclaim their mobile privacy and improve their smartphone’s security along the way.
With Google’s products, it’s never a good idea to hop on the latest release right away, as proven in the past. Hence it only makes sense to upgrade to the previous, more battle-tested version – if you must upgrade in the first place.
I decided to upgrade from my Pixel 6a to the Pixel 8 roughly three months ago and have been using the device with GrapheneOS from day one. My main reason for upgrading was the declining battery life and a crack in the screen, which initially didn’t seem like a big deal, but eventually turned out to be an issue in regard to moisture/humidity. However, if I hadn’t found an absolutely bonkers deal on the Pixel 8 I probably wouldn’t have upgraded either.
Note
According to the UN Global E-Waste Monitor 2024 report, the world went from 34 billion kg of e-waste per year, which was generated back in 2010, to a record 62 billion kg globally per year in 2022 – out of which approximately 901 million kg were phones. With only 22.3% of the e-waste being collected and recycled in an environmentally sound manner – however that might be interpreted by individual jurisdictions – the growth of e-waste generation has outpaced its collection and recycling by almost a factor of 5 since 2010.
One contributing factor that I believe plays a part in this is the consumerist mentality propagated by modern media, first and foremost social media. Technological advancements are merely the reason for people to upgrade consumer electronics anymore. Instead, it appears to be the never-ending chase and thereby induced appetite for the shiny new thing, that is predominantly cultured by “Tech YouTubers” and influencers alike.
If you have no reason to upgrade a device, do not upgrade it. Neither generation of any phone will have real technological advancements over its previous generation. If you nevertheless decide to upgrade, do not toss the old device: Repurpose it. If it has a decent camera, use it as a dedicated webcam. If the camera is just okay, convert it to a car dash-cam or a home security camera with integrated UPS, storage, and even fallback connectivity via mobile networks. Use it as a dedicated gaming device, or a music player for non-IoT speakers. Convert it to an LTE modem and make it a fallback for your home internet. Run a Monero node on it. Or a Briar mailbox. Host a personal website on it and make it available via DynDNS. Make use of the phone’s sensors, e.g. the light sensor or the microphone for home automation. Connect it to speakers and use it as a Bitcoin price monitor that plays “You Suffer” by Napalm Death every time BTC passes a certain threshold. Or just use it as a digital photo frame on your desk. And if you really can not find a use for it, try to sell it or, even better, donate it.
Tl;dr: The Pixel 8 of today is a solid piece of hardware if you happen to
find a fully functional device. As with most Google products, quality control
with the Pixel series hasn’t been the center point of attention, hence you might
end up with a device with random defects, like hardware-related ghost touches or
broken speakers.
GrapheneOS, on the other hand, is just as great on the Pixel 8, as it has been
on the 6a – but significantly snappier. GPS appears to be significantly faster
and more accurate, and battery life is fairly good with roughly six hours of
screen time over two days of normal use (without battery saver).
Hardware

The Pixel 8 features a sleek and modern design that maintains Google’s design language – which, frankly, I’m not the biggest fan of. However, I do like the hazel color of the Pixel 8, which resembles a muted camouflage green. At 150.5mm x 70.8mm x 8.9mm and 187g, the device is fairly compact and lightweight.
The phone sports a 6.4-inch 20:9 OLED display with a 1080x2400px resolution and a variable refresh rate between 60Hz and 120Hz. Screen brightness goes up to 1400 nits for HDR content, and up to 2000 nits peak brightness. The screen is protected by Gorilla Glass’ Victus glass, but as with every other phone display, I wouldn’t dare to test its durability.
Under the hood, the Pixel 8 is powered by the Google Tensor G3 processor, paired with their Titan M2 security coprocessor and 8GB of LPDDR5X RAM. The device is available with either 128 GB or 256 GB UFS 3.1 storage – I opted for the cheaper 128 GB variant.
The 5000mAh battery delivers enough power for two days of light to moderate use and can be recharged at 30W within approximately one and a half hours. Compared to my aged Pixel 6a I seem to be getting maybe half a day more runtime out of the phone.
The Pixel 8 comes with two cameras on the back – a 50MP main sensor and a 12MP ultra-wide sensor – and a 10.5MP selfie camera in the front. The main camera has an ƒ/1.68 aperture and an 82° field of view. The ultra-wide camera on the other hand has an ƒ/2.2 aperture and a 125.8° field of view. Similarly, the selfie camera also comes with a ƒ/2.2 aperture, but at a 95° ultrawide field of view.
The rear, as well as the selfie camera, can booth shoot 4K video at up to 60 FPS. Considering the solid photo and video quality I was able to get out of the Pixel 6a, the Google Pixel 8 cameras don’t wow me in particular. They are nevertheless an improvement over the 6a cameras, especially in low-light conditions.
As for connectivity, the Pixel 8 supports LTE and 5G, WiFi 7 (802.11be), and Bluetooth v5.3. One thing that the Pixel 8 is significantly better at is GPS. While the 6a always struggled to catch usable GPS signals even outdoors at times, I can easily fire up Organic Maps while still indoors and it will give me my exact location within seconds.
Note
I’m not using any of Google’s location enhancement services on GrapheneOS, meaning that the phone relies on solely the GPS signal.
The Google Pixel 8 has an iFixit repairability score of 6/10, placing it slightly above the 6a and 6 Pro, the 7 and 7 Pro (5/10), and the 7a (4/10), making it on par with the 6 and the 8 Pro.
Installation

As with the Google Pixel 6a, installation is a breeze. Using Chromium, I was able to run the GrapheneOS WebUSB installer and flash the de-googled operating system onto the phone in a matter of minutes.
Upon first boot, the user is greeted with the Welcome screen and a setup wizard that guides through things like WiFi configuration, passcode/fingerprint setup, and all that. It’s a straightforward process that every Android user should be familiar with.
First things first
As soon as the setup wizard is finished and the bootloader is locked, the phone can be properly configured and set up.
eSIM
If you require eSIM support, you have to enable it under Settings > Network & internet > eSIM support. Enabling eSIM support will require a device restart and will enable proprietary Google functionality needed to provision and manage eSIMs. You can find out more about eSIM support here.
Generally, I advise against the use of eSIMs, as they come with significant disadvantages over SIM cards. First and foremost, eSIM activation often only works within the carrier network. There are numerous reports on Reddit of Google Fi users who used an eSIM and had to factory reset their smartphone while outside of the US, leaving them with no service, because the eSIM could only be re-activated while in the US.
Also, especially in less developed countries, eSIMs usually aren’t available and if they are, they are only available for long-term post-paid contracts. Being a big advocate for no-obligations pre-paid throwaway cards that ideally have little to no KYC requirements, I don’t appreciate the direction in which carriers and smartphone manufacturers are pushing with eSIMs. Most eSIM options globally have tight KYC requirements. As long as I cannot have dynamic identifiers (IMSI, Ki, IMEI) – it has been tried – I would at least like to not have my full details, a copy of my passport, and my banking information stored right next to these identifiers in some carrier’s database. Not only because I like my privacy, but because the people tasked with protecting this data don’t appear to be the sharpest knives in the kitchen.
Repositories
After successfully connecting the device to the internet in one way or another, it’s time to install some basics. The first thing you’ll want to do is go to the F-Droid website and download the latest version of the app, using Vanadium, which is GrapheneOS’ standard (pre-installed) browser. You will have to allow packages downloaded via Vanadium to be installed, but you can revert that setting after F-Droid is ready to go.
On F-Droid, you will likely want to add a few important repositories:
- Cromite, an up-to-date fork of the no-longer-maintained Bromite browser
- FUTO, the repository of the organization building the FUTO Keyboard, FUTO Voice, and GrayJay, amongst many other apps
- The Guardian Project, for apps like Tor Browser, Orbot, and many others
Optionally, you might want to add the following repositories if you’re using either of these messengers:
- Briar, the censorship-resistant peer-to-peer messenger
- Session, the decentralized Signal alternative built on top of the Oxen network/Lokinet
- Molly-FOSS, the independent Signal fork with a focus on security
Essentials
With the repositories in place, I recommend installing the following apps:
- Cromite, as mentioned before, is a continuation of Bromite and a great Android browser with integrated AdBlock and various privacy enhancements.
- FUTO Keyboard, also mentioned before, is probably the best open-source, privacy-respecting Android keyboard with swipe support out there. In addition, it has Voice-to-Text that works fully on-device (nothing is sent to cloud services).
- Tor Browser and Orbot, for browsing and proxying other apps through the Onion network.
- Aves Libre, probably the best open-source gallery app on Android.
- Binary Eye, a QR- and barcode scanner.
- Breezy Weather, probably the best weather app for Android.
- Grayjay, as mentioned previously, is a client for popular video platforms like YouTube, Odysee, and others.
- Hypatia, a real-time malware scanner.
- K-9 Mail, soon Thunderbird for Android, is probably the most feature-rich open-source e-mail client for Android.
- LocalSend, an app for sharing files peer-to-peer with other Android and iOS phones, as well as Linux, Windows, and macOS computers.
- OnionShare, an app for sharing files securely and anonymously via the Tor network.
- Organic Maps, like Google Maps but open-source and based on OpenStreetMap.
- PixelKnot, an F5 steganography app that allows embedding secret messages into pictures.
- Syncthing, a peer-to-peer file synchronization app that allows building your own decentralized Dropbox.
- Tasks, a private to-do app that supports CalDAV and EteSync.
- Termux, a terminal emulator for Android.
- VLC, the famous video and audio player.
Push notifications
As I do not recommend installing Google Play services, push notifications should be enabled via UnifiedPush. Many open-source apps already support UnifiedPush. In case you will be using Conversations as an XMPP messenger, you already have a distributor app at your disposal. Otherwise, ntfy might be for you.
A list of all apps supporting notifications via UnifiedPush can be found here. All other apps will not be able to send you instant push notifications unless they sport a custom implementation that is likely to kill battery life. However, many apps might allow for periodic notifications, by scheduling checks to their respective server for new events. However, with research suggesting that push notifications are in fact bad for us, it’s advantageous to only have limited support for it.
Additional apps
One important piece of software on a phone is the launcher. The GrapheneOS/Android stock launcher is relatively meh. It does the job, but it lacks various features that I and probably many others appreciate.
Hence, I use Lawnchair. The latest release available at the time of writing is 14 Beta 2, which, despite its name, runs perfectly fine and stable.
Another app you might want to get is the Markup app, that you can get via GrapheneOS’ App Store app. It does not require Google Play services or network access. When installed, adjusting, for example, screenshots (power button + volume down button) becomes a lot less cumbersome. Markup is the standard image editor on Pixel OS, by Google.
Depending on whether you find all the apps you need on F-Droid or might require closed-source apps from the official Play Store, you will have to install Aurora Store. Aurora works without Google Play services and doesn’t require a Google account to function. However, bear in mind that all apps downloaded via Aurora are coming from Google’s official Play Store and might hence be malware.
Note
GrapheneOS now comes with Accrescent (installable through its App Store app), which is a privacy- and security-focused alternative to the Play Store. So far, all of the apps on Accrescent seem to also be available through F-Droid.
For a list of other apps that might be interesting to you, check my phone page.
Configuration
I won’t be going through all the configuration options of Android, however, GrapheneOS has a handful of interesting settings that are worth mentioning. Apart from obvious ones like Settings > Security > Screen lock, as well as Settings > Security > USB-C port, there are a handful of features that are particularly useful in everyday use.
Scramble PIN layout
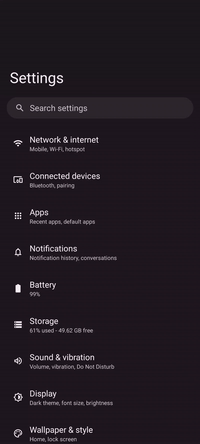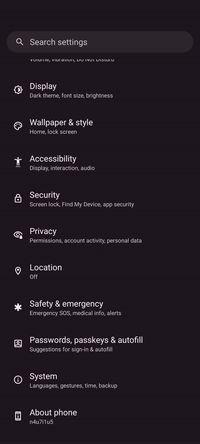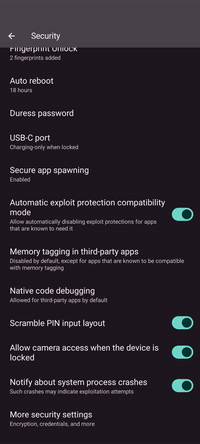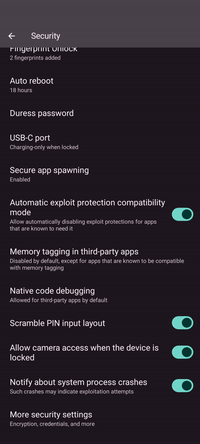
If you’re using a PIN to unlock your phone, scrambling the PIN layout on the lock screen helps to prevent others from finding out your PIN by looking at your thumb movements or by investigating your screen for oil residues from repeated taps on specific areas.
Secure App spawning
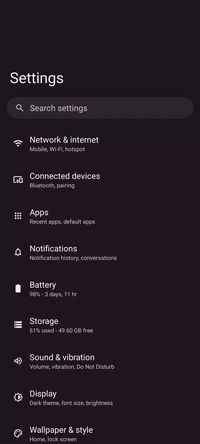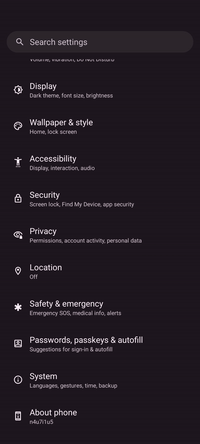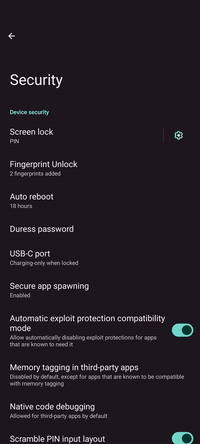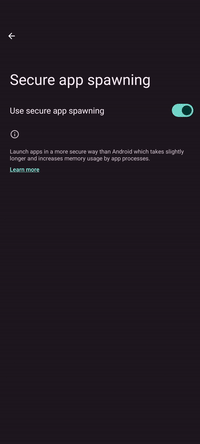
Enabling this setting improves privacy and security at the expense of a higher cold start time and RAM footprint for apps. Refer to the exec spawning documentation for more information.
Auto reboot
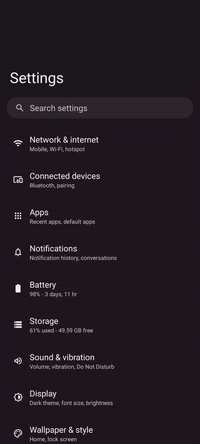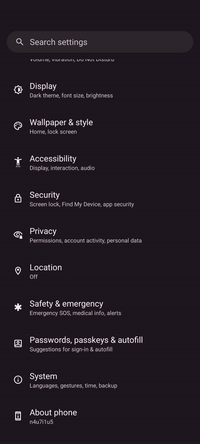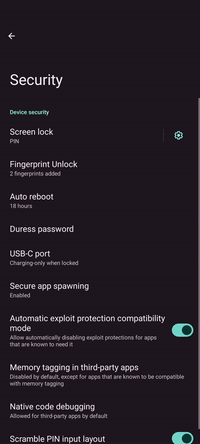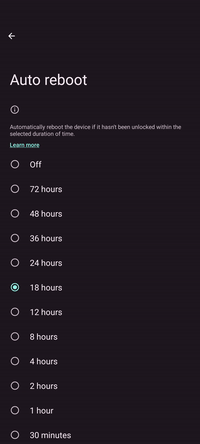
This nifty feature automatically reboots the device if it has not been unlocked for a specified amount of time, to put data at rest and remove any app data from RAM. It offers another protection layer for scenarios in which the device is stolen or lost or in case the device owner becomes incapacitated.
Duress password
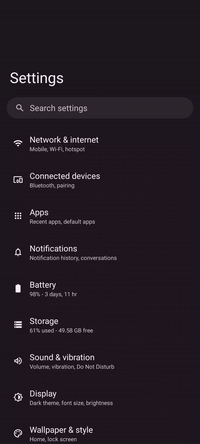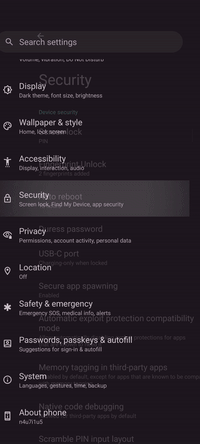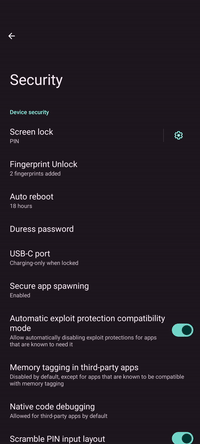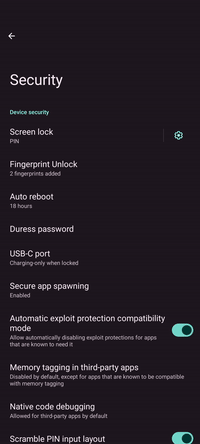
Duress password is a useful feature for scenarios in which the device owner is forced to hand over the device. By having a duress PIN or password set, the device will not grant access but instead wipe itself when unlocked with it. In a hostile scenario, it can be used to make sure that personal information on the device is destroyed.
Think of being caught up in a robbery, in which the attacker(s) demand(s) your mobile device. Quickly tapping the duress PIN or password while handing over the hardware can make sure that no personal information can ever be extracted from it.
Another scenario would be an unwarranted request to access your phone’s data. By handing over the device and unlocking it using the duress PIN or password, the device can be rendered useless within seconds.
FAQ
Frequently asked questions that usually come up when considering switching to GrapheneOS.
Can I use WhatsApp/Telegram/Signal/Threema/Wire/Kik/Viber/… on GrapheneOS?
Well, yes, most of these spywares messengers work. Some of them even deliver
notifications through own push implementations – which will however have an
impact on battery life – and for Telegram there are FOSS client apps available
on F-Droid. Having that said, I do not recommend using any of these messaging
platforms.
Instead, have a look at privacy-preserving alternatives, or set up your own messaging service. If you must use Signal, use Molly.
Can I use TikTok/Snapchat/Instagram/Facebook/… on GrapheneOS?

In theory, all of these apps work on GrapheneOS. I do however strongly encourage you to learn about what TikTok, Snapchat, Instagram, and Facebook are doing behind your back. I strongly advise against installing any of these apps on your GrapheneOS phone, unless you know what you’re doing.
If you’re looking for alternatives, you might want to check Pixelfed and Circles. If you want to keep up a controlled, public version of your profile on big tech social media, use a secondary, stock OS device to install the apps onto.
Can I use Discord on GrapheneOS?
Yes, but as mentioned under Push Notifications, without Google Play services notifications won’t work. There are however great alternatives to Discord, namely Element/Matrix, and XMPP. If you are a community administrator I recommend migrating to Matrix (the network behind Element) and starting by bridging your Discord channels into Matrix rooms.
Can I use YouTube on GrapheneOS?
Yes, and it’s even better than the official YouTube app. Grayjay, as well as NewPipe, and LibreTube offer an improved experience with features like picture-in-picture and background audio-only playing, as well as integrations into other platforms like Odysee, Twitch, PeerTube, and many more.
Can I use my Revolut/Wise/BofA/… banking app on GrapheneOS?
It depends, as many of these apps have anti-tampering mechanisms in place and increasingly depend on Google Play Integrity. Refer to this post for more info.
In any way, banking apps will likely require Google Play services to be installed underneath the same profile. Although there is a website listing compatible banking apps, upon further inspection it shows that more often than not running these sorts of apps requires disabling the very features that make it worth using GrapheneOS in the first place. Hence YMMV.
However, given that you are likely to own a mobile device from which you would upgrade, I recommend using that device as a consciously insecure platform and running banking apps off of its stock iOS or Android operating system, making it a dedicated non-free spyware device. The keyword here is compartmentalization: Limit access to information on a need-to-know basis.
Your bank already knows everything about you, there is no point in running its app off of a privacy-protecting mobile device. At best, you will gain the comfort (?) of not having to use two phones for different tasks, but in the worst case, you might jeopardize the security of everything else on that same phone by disabling protections that GrapheneOS has intentionally put in place.
Can I use Android Auto on GrapheneOS?
Yes, GrapheneOS supports Android Auto. It can be installed through its app store and it requires Google Play services. Even though the GrapheneOS team does a terrific job in restricting/sandboxing Android Auto, I would nevertheless recommend using a dedicated non-free spyware device for Android Auto (see banking).
The reason for that is first and foremost to avoid having Google Play services installed. However, besides that, I would argue that Android Auto is of no use on a device that tries to be as free of big tech apps as possible. Most apps on the F-Droid store won’t support Android Auto, e.g. for playing music. Even when they do, it’s usually not the smoothest experience one might expect, especially during driving.
Besides, bear in mind that keeping your phone connected via USB to a head unit and hence charging for prolonged periods will result in a decline in battery capacity and performance. This is true for Android Auto as it is for Apple CarPlay. Using the wireless Android Auto on the other hand can be a PITA, depending on the car, and hence might require additional hardware like an AAWireless or Motorola MA1 adapter. Additionally, wireless Android Auto is usually battery intensive and will drain your phone on longer trips significantly.
Long story short, having a dedicated Idgaf device that can stay connected to your car and can use all the privacy-invasive apps that make sense for proprietary platforms like car entertainment systems sounds like a more reasonable solution. And if you’re worried about Samsung, Google, or any other stock Android smartphone tracking your every move when you’re driving, rest assured: The manufacturer of your Android Auto-capable car already does so and likely sells your data, through data brokers, to big tech anyway. It’s a naive fallacy to think that GrapheneOS will be a silver bullet for protecting your privacy and security when connecting and using it in a completely closed-source, proprietary platform like a modern car.
Why GrapheneOS instead of /e/OS, DivestOS, CalyxOS, IodeOS, etc.?
Unlike other projects, GrapheneOS is the only Android-based operating system that truly focuses on strong security and freedom (from proprietary software). Not only is it quicker to update to the latest Android release than others, but in some cases, GrapheneOS delivers patches even before upstream does. Unlike other projects, Graphene uses hardened versions of the Android WebView, the Linux kernel, and the memory allocator. And unlike /e/OS or CalyxOS, GrapheneOS doesn’t come with either microG, a service that uses proprietary Google binaries, or Google Play services pre-installed.
Especially when going into the nitty gritty details of the inner workings of the mobile device, it becomes quite evident that the GrapheneOS team does the due diligence thoroughly, unlike ROMs that at times fail to provide precise answers to important questions and, more importantly, private and secure solutions.
Here is one example of how the CalyxOS ROM handles things:
What is Qualcomm doing?
We don’t exactly know, because this is handled inside the baseband processor (a separate computer on your device that handles all the radios and wireless networking). The domain xtrapath1.izatcloud.net is used by the baseband to load a data file of GPS satellite positions. Unfortunately, this data is downloaded over plain text HTTP, and it’s use and parsing is handled by the “black box” of the baseband, which runs proprietary software and which we have no visibility into what it is actually doing.
This is from the Qualcomm privacy notice:
The Qualcomm GNSS Assistance Service downloads to your device a data file from QTI containing the predicted orbits of the Global Navigation Satellite System (GNSS) satellites. The Qualcomm GNSS Assistance Service also uploads a small amount of data to us comprised of: a randomly generated unique software ID that is not associated to you or to other IDs, the chipset name and serial number, the Qualcomm GNSS Assistance Service software version, the mobile country code(s) and network code(s) (allowing identification of country and wireless operator), the type of operating system and version, device make and model, the date and time of connection to the server, the time since the last boot of the application processor and modem, and a list of QTI software on the device
In the future, we may choose to block this domain, causing longer initial location resolution when using GPS.
(Source: CalyxOS documentation)
And here is the same situation handled by GrapheneOS:
HTTPS connections are made to fetch PSDS information to assist with satellite based location. These are static files and are downloaded automatically to improve location resolution speed and accuracy. No query or data is sent to these servers. These contain orbits and statuses of satellites, Earth environmental data and time adjustment information.
On the Pixel 8a (which uses a Samsung GNSS chip), almanacs are downloaded from https://samsung.psds.grapheneos.org/p4/42F3 which is a cache of Samsung’s data. Alternatively, the standard servers can be enabled in the Settings app which will use https://1.ssiloc.com/p4/42F3.
On 6th generation Pixels onwards (which use a Broadcom GNSS chip), almanacs are downloaded from https://broadcom.psds.grapheneos.org/lto2.dat, https://broadcom.psds.grapheneos.org/rto.dat and https://broadcom.psds.grapheneos.org/rtistatus.dat which are a cache for Broadcom’s data available at https://gllto.glpals.com/7day/v5/latest/lto2.dat, https://gllto.glpals.com/rto/v1/latest/rto.dat and https://gllto.glpals.com/rtistatus4.dat. Alternatively, the standard servers can be enabled in the Settings app which are https://agnss.goog/lto2.dat, https://agnss.goog/rto.dat and https://agnss.goog/rtistatus.dat providing a similar cache of Broadcom’s data currently (as of October 2022) hosted on GCP (Google Cloud Platform).
On 4th and 5th generation Pixels (which use a Qualcomm baseband providing cellular, Wi-Fi, Bluetooth and GNSS in separate sandboxes), almanacs are downloaded from https://qualcomm.psds.grapheneos.org/xtra3Mgrbeji.bin which is a cache of Qualcomm’s data. Alternatively, the standard servers can be enabled in the Settings app which will use https://path1.xtracloud.net/xtra3Mgrbeji.bin, https://path2.xtracloud.net/xtra3Mgrbeji.bin and https://path3.xtracloud.net/xtra3Mgrbeji.bin. GrapheneOS improves the privacy of Qualcomm PSDS (XTRA) by removing the User-Agent header normally containing an SoC serial number (unique hardware identifier), random ID and information on the phone including manufacturer, brand and model. We also always fetch the most complete XTRA database variant (xtra3Mgrbeji.bin) instead of model/carrier/region dependent variants to avoid leaking a small amount of information based on the database variant.
Qualcomm Snapdragon SoC devices also fetch time via NTP for xtra-daemon instead of using potentially incorrect OS time. We use time.grapheneos.org when using the default GrapheneOS PSDS servers or the standard time.xtracloud.net when using Qualcomm’s servers. Stock Pixel OS uses time.google.com but we follow Qualcomm’s standard settings to match other devices and to avoid the incompatible leap second handling. These connections all go through the Owner VPN so it isn’t a real world fingerprinting issue.
(Source: GrapheneOS FAQ)
Just the sheer level of detail that GrapheneOS goes into shows the difference in carefulness and commitment that it has towards privacy and security topics, in comparison to other projects.
For an overview of the high-level differences between projects, see this website. For an in-depth analysis of individual projects, check the blog of Mike Kuketz, an IT security researcher and pentester:
- Android: GrapheneOS, CalyxOS and Co. under the microscope – Custom-ROMs Part1
- CalyxOS: De-Googled is different – Custom-ROMs Part2
- iodéOS: Privacy-friendly, but compromises in security – Custom-ROMs Part3
- LineageOS: Neither secure nor privacy-friendly – Custom-ROMs Part4
- DivestOS: Privacy-friendly and increased security – Custom-ROMs Part5
- /e/: Privacy-friendly does not necessarily mean secure – Custom-ROMs Part6
- GrapheneOS: The gold standard among Android ROMs – Custom-ROMs Part7
Hint
Titles were translated using Firefox Translate, Mozilla’s offline translation feature. Use it to translate the posts into your preferred language.
The final verdict of the author’s heptalogy summarizes the current environment perfectly:
GrapheneOS sets standards in terms of security and privacy that are not achieved by any other Android system. […] There is no doubt that GrapheneOS is currently the safest and most privacy-friendly custom ROM Android system there is. It would be the icing on the cake if the requirement to use a Google device was lifted and GrapheneOS had plans to bring its own devices to market. This is actually the only point where I would have to criticise something – complaining on a high level.
But <insert YouTuber here> recommends <insert project here>!
With all due respect to the creators’ achievements, when looking at many of their public résumés (mainly LinkedIn, and, if even available, OSS contributions), hardly any of them appear to be particularly qualified to speak on the topics of system hardening, Android development or security research in general.
None of the popular videos on YouTube that I found on this topic mentions to have been created in collaboration with a knowledgeable person from any of the relevant areas, or at least even just based on credible sources from the fields. In addition, I did not find any indication of the creators or their teams being able to deep-dive into implementations and due diligence on any of the solutions they are recommending. Most recommendations hence seem to come from either partnerships with individual projects, or purely out of the projects’ marketing materials. Many projects however fail to live up to the hype and, in contrary to what they promise, even impose additional risks to the user, be it due to delayed or lacking security patches, unlocked bootloaders, or other circumstances that might put the end-user security and privacy in danger.
GrapheneOS, on the other hand, has demonstrated continuously that its development efforts not only scratch the surface of Android security but effectively lead to actual vulnerabilities being exposed, reported, and ultimately fixed.
While anyone regardless of their background might have the desire to use software that respects their privacy and offers sufficient security, not everyone is capable of investigating these topics and making an informed recommendation to others. As usual with recommendations, in particular, coming from people who make their living in entertainment, it is important to be critical about their claims, especially when they have no evident background in the area they are covering. What I noticed during info gathering for this post was that pRiVaCy YoUtUbErS appear to have amongst the least in-depth knowledge of computer system inner workings, programming, and security topics – yet they throw around big claims (with no evidence to back them) and somehow gamble the YouTube algorithm well enough to almost always have their videos be shown amongst the first few search results for any privacy or security-related topic.
These days, privacy is the snake oil that can make a lot of money, not only by selling subscriptions to VPN services, mail providers, and password managers, but also by advertising dubious browsers, access to mindless Discord echo chambers, or even pReMiUm CoUrSeS on how to be sEcUrE, pRiVaTe AnD aNoNmYoUs.
As a rule of thumb
If a recommendation is coming from someone with no in-depth experience in the field, and with no references to sources with in-depth knowledge in the field, it is hardly ever legit. Getting privacy or security advice from YouTubers is, in most cases, like getting medical advice from Alex Jones.
Will GrapheneOS protect me from government spyware (Pegasus, Cellebrite, etc.)?
GrapheneOS is not immune to such software, especially when used by government actors. However, so far the project’s track record for defending against these tools has been one of the best in the Android market. Given a sane configuration of settings (e.g. Wi-Fi calling and USB connections), as well as a sensible approach to app installations and web browsing behavior, GrapheneOS will likely be the best option to protect you from a wide variety of threats.
Having that said, it’s worth remembering that threat protection is an inherently unequal game, in which the threat actors have access to and can experiment with GrapheneOS, while the GrapheneOS team does not have access to the threat actors' tools. Hence it is impossible to foresee, let alone guarantee successful threat protection in every scenario.
Will GrapheneOS protect me from crypto-malware and viruses?
GrapheneOS reduces the attack surface that these programs have, but there is no silver bullet against either of them. Turning on your brain when surfing the web, downloading and installing apps, and opening e-mail attachments is probably the best way to protect yourself from these threats. In addition, Hypatia is a solid malware scanner that you should run from time to time.
Will GrapheneOS protect me from Daniel Micay breaking into my house, crapping in my hallway, and unscrewing my lightbulbs?
Although there’s a non-zero probability that this might happen, I wouldn’t worry too much, especially with GrapheneOS running on your phone. At least that’s what YouTube taught me.
Okay, where do I start?
Install GrapheneOS
Enjoyed this? Support me via Monero, Bitcoin or Ethereum! More info.